A strategy designed to restore data and systems following a ransomware attack is critical for business continuity. This involves a structured approach that outlines procedures for identifying the attack, isolating affected systems,... Read more »

A template for restoring information technology infrastructure and operations after an unforeseen disruptive event provides a structured approach to minimizing downtime and data loss. Such a template typically includes documented procedures for... Read more »

A documented process enabling organizations to resume mission-critical functions following disruptive events like natural disasters, cyberattacks, or equipment failures involves restoring data, applications, and infrastructure to operational status. A practical illustration involves... Read more »

Swift identification of disruptive events, whether natural disasters, cyberattacks, or hardware failures, is paramount for effective disaster recovery. This allows organizations to initiate recovery processes promptly, minimizing downtime and potential data loss.... Read more »

A template document in Portable Document Format (PDF) provides a pre-designed framework for organizations to create a strategy for restoring critical operations and data after an unforeseen disruptive event. This framework typically... Read more »

Organizations depend on their information systems and operational processes. A framework designed to safeguard these critical functions against disruptions involves two key components. The first focuses on restoring IT infrastructure and systems... Read more »

The ability of an organization to resume operations after a disruptive eventnatural or human-madeis critical to its survival. This resilience is achieved through a documented strategy that outlines processes, procedures, and resources... Read more »
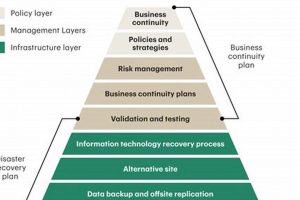
Organizations rely on processes and resources to function effectively. Protecting these vital components from disruption requires a structured approach to ensure operational resilience. This involves developing strategies to mitigate risks, respond to... Read more »
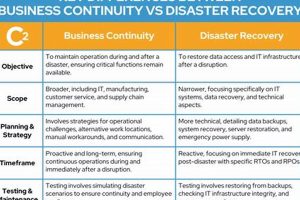
A disaster recovery strategy focuses on restoring IT infrastructure and operations after a significant disruption, such as a natural disaster or cyberattack. It typically involves detailed procedures for recovering data, applications, and... Read more »

Aviation accidents within Scotland’s borders encompass a range of incidents, from small private aircraft crashes to larger commercial tragedies. These events can involve various contributing factors, including mechanical failure, human error, and... Read more »