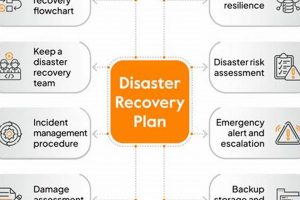
A structured approach that enables organizations to resume mission-critical functions following disruptive events involves preemptive planning, mitigation strategies, and post-incident restoration procedures. For example, a company might replicate its data in a... Read more »
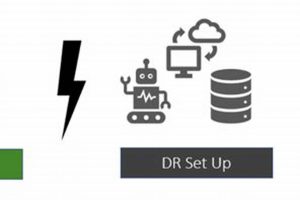
Automating business processes through software robots offers significant efficiency gains, but these systems are not immune to disruptions. A plan to reinstate these automated processes swiftly and reliably following an unforeseen event,... Read more »

Restoring technological infrastructure and data after unforeseen events, such as natural disasters, cyberattacks, or hardware failures, is a critical process for any organization. A robust plan enables the resumption of business operations... Read more »

A business continuity strategy that enables the restoration of vital IT infrastructure and systems following a disruptive event is crucial for organizational resilience. This involves replicating data and systems to an alternate... Read more »

Maintaining uninterrupted communication is crucial for businesses, particularly those relying heavily on phone systems for operations. When unforeseen events like natural disasters, cyberattacks, or hardware failures disrupt telephony services, the ability to... Read more »

Organizations rely on digital infrastructure and data for daily operations. Unforeseen events like natural disasters, cyberattacks, or hardware failures can disrupt access to these vital resources, leading to significant financial losses, reputational... Read more »
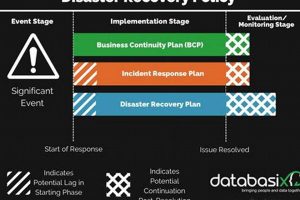
A documented, structured approach ensuring an organization’s ability to resume critical functions following a disruptive event whether natural, technical, or human-caused forms the core of business continuity planning. This documented approach typically... Read more »
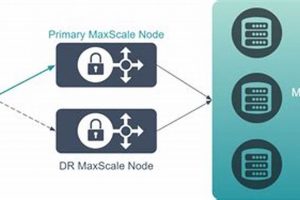
Protecting critical business operations relies on ensuring the continuous availability of essential platforms. For organizations that depend on ServiceNow for IT service management, HR, security, and other crucial functions, a robust plan... Read more »
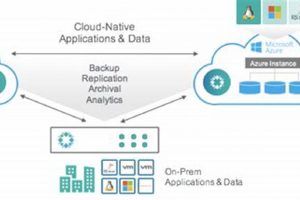
Data protection against catastrophic events is paramount for business continuity. A modern approach to this challenge utilizes a cloud data management platform that simplifies and automates the process of protecting, recovering, and... Read more »

Protecting digital assets involves two key processes: regularly copying information to a separate, secure location and having a comprehensive plan to restore functionality after unforeseen events. For example, a business might copy... Read more »