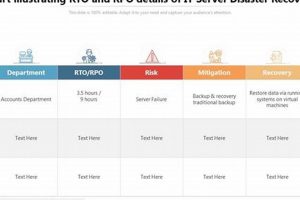
Recovery Point Objective (RPO) represents the maximum acceptable data loss an organization can tolerate following a disruptive event. It’s measured in units of time, such as minutes, hours, or days. For instance,... Read more »

A planned simulation of emergency procedures assesses an organization’s ability to respond to significant disruptions. For example, such a simulation might involve restoring data from backups, activating alternate work locations, or testing... Read more »

Data protection involves two distinct but related concepts: creating copies of data and restoring access to IT infrastructure after an outage. The former focuses on preserving information by regularly copying files and... Read more »
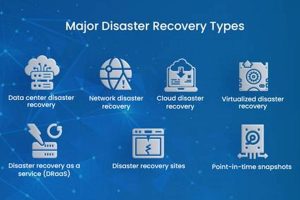
Specific vocabulary exists to describe the processes, technologies, and strategies involved in resuming business operations after an unforeseen disruptive event. For instance, “Recovery Time Objective” (RTO) defines the maximum acceptable duration of... Read more »

Protecting critical business data is paramount in today’s digital landscape. A robust plan to restore a customer relationship management (CRM) system after an unforeseen event, such as a natural disaster, cyberattack, or... Read more »
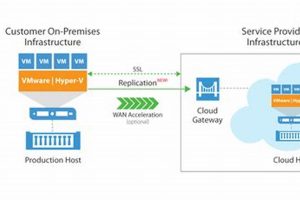
Data loss and extended downtime can cripple an organization. Protecting against such scenarios requires a robust strategy that ensures business continuity. A comprehensive approach involving backups, replication, and orchestration enables rapid restoration... Read more »
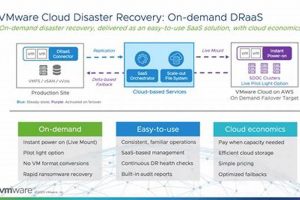
Protecting vital digital assets against unforeseen events is paramount in today’s interconnected world. A robust solution for ensuring business continuity involves replicating and recovering virtualized infrastructure in a secure cloud environment. This... Read more »
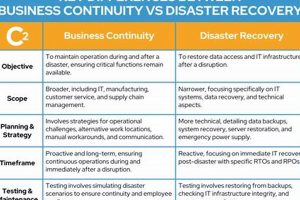
Organizations depend on their ability to function continuously. Maintaining operational resilience involves planning for unforeseen disruptions and establishing procedures to recover quickly. Imagine a company whose primary data center experiences a power... Read more »
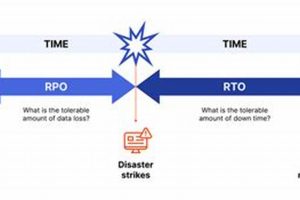
Recovery Point Objective (RPO) and Recovery Time Objective (RTO) are two crucial metrics used in business continuity and disaster recovery planning. RPO determines the maximum acceptable data loss in the event of... Read more »

A robust approach to verifying the effectiveness of plans for restoring critical IT infrastructure and data after disruptive events involves meticulous planning, execution, and evaluation of various recovery scenarios. For instance, a... Read more »