Environmental remediation and engineering firm Tetra Tech offers comprehensive services designed to help communities and businesses prepare for, respond to, and recover from natural and human-caused disasters. These services typically encompass a... Read more »
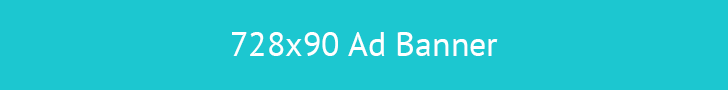
Protecting vital data and ensuring business continuity are paramount in today’s digital landscape. A robust plan to restore IT infrastructure after unforeseen events like natural disasters, cyberattacks, or hardware failures is essential.... Read more »
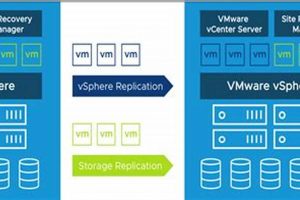
A partially equipped facility, maintained in a state of readiness, allows an organization to resume operations following a disruption. This setup typically includes pre-installed hardware, software, and network connectivity, though some configurations... Read more »

A chronological record of planning, testing, and execution activities related to restoring IT systems and business operations after disruptive events provides an invaluable resource. This documentation typically includes details like system configurations,... Read more »
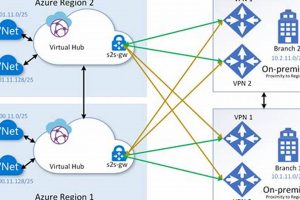
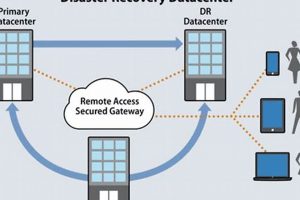
Cloud-based business continuity and resilience are achieved through a collection of tools and services that allow replication, failover, and recovery of applications and data to a secondary, geographically separate Azure region. For... Read more »

Restoring operations after unforeseen events like natural disasters, cyberattacks, or equipment failures is crucial for any organization, but particularly for smaller enterprises. Imagine a local bakery losing its customer data due to... Read more »
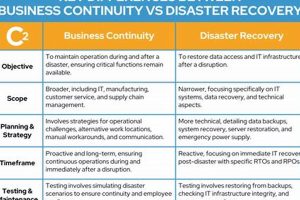
While both are crucial for organizational resilience, they address different aspects of disruption. Disaster recovery focuses on restoring IT infrastructure and systems after a significant outage, such as a natural disaster or... Read more »
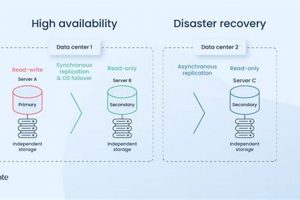
Protecting critical systems and data involves two distinct but related concepts: resuming operations after a catastrophic event and ensuring uninterrupted service during normal operations. The former focuses on restoring functionality after significant... Read more »
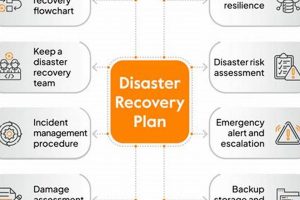
A documented, structured approach ensures the continuity of critical technology infrastructure and data following disruptive events, such as natural disasters, cyberattacks, or equipment failures. This approach typically involves detailed plans for data... Read more »

The process of safeguarding an organization from significant negative events that could disrupt operations is crucial for business continuity. This involves developing and implementing strategies to restore critical IT infrastructure and business... Read more »