The location in Lakehurst, New Jersey, where the German passenger airship LZ 129 Hindenburg caught fire and crashed on May 6, 1937, is a significant historical landmark. The incident, captured in dramatic... Read more »

Published accounts of the 1937 airship tragedy range from meticulously researched historical analyses to personal narratives of those affected. These accounts offer varying perspectives on the event, including technical explanations of the... Read more »

May 6, 1937, marks the day the German passenger airship LZ 129 Hindenburg caught fire and crashed in Lakehurst, New Jersey. This catastrophic event, widely documented in photographs and newsreels, brought an... Read more »

Positions related to storm disaster response encompass a wide range of specializations, from immediate rescue and relief efforts to long-term recovery and reconstruction. These roles may involve providing emergency medical services, clearing... Read more »

The November 5, 1983, incident aboard the Byford Dolphin semi-submersible drilling rig in the Frigg gas field of the North Sea resulted in the deaths of five divers. During a routine saturation... Read more »

The tragedy that unfolded in Bhopal, Madhya Pradesh, India, in December 1984, resulting from a methyl isocyanate gas leak at a Union Carbide India Limited pesticide plant, remains one of the world’s... Read more »
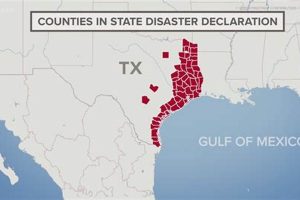
A gubernatorial proclamation of a state of disaster in the Lone Star State activates emergency resources and waives certain regulations to facilitate a swift response to events such as hurricanes, floods, wildfires,... Read more »

The catastrophic events on K2, the world’s second-highest mountain, during the first week of August 2008, resulted in the deadliest single accident in the mountain’s climbing history. A series of events, including... Read more »

Super Bowl XXXIX, held in Jacksonville, Florida in 2005, is often remembered for logistical challenges surrounding the event. These included significant traffic congestion, limited parking availability, and inadequate public transportation options that... Read more »

A selection process for new National Basketball Association (NBA) players that yields unexpectedly poor results, significantly impacting a team’s performance for years to come, can be categorized as a severely flawed recruitment... Read more »