A sample strategy for restoring IT infrastructure and operations after a disruptive event typically includes elements such as identifying critical systems, establishing recovery time objectives, outlining backup procedures, and defining communication protocols.... Read more »

A comprehensive plan for restoring critical data and systems following unforeseen events, such as natural disasters, cyberattacks, or hardware failures, ensures business continuity. This plan typically involves regular data backups, secure offsite... Read more »
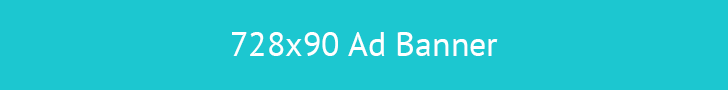
Protecting an organization’s data and IT infrastructure is paramount in today’s digital landscape. A strategy involving off-site servers to safeguard and restore data and applications in the event of a catastrophe, such... Read more »

A pre-designed blueprint for restoring IT infrastructure and operations after an unforeseen disruptive event, such as a natural disaster or cyberattack, demonstrates how an organization can systematically resume critical functions. A sample... Read more »

Organizations rely on intricate technological systems for daily operations. When unforeseen events disrupt these systems, the potential for significant financial loss and reputational damage is substantial. Firms specializing in business continuity offer... Read more »
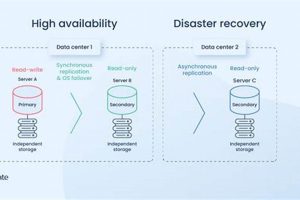
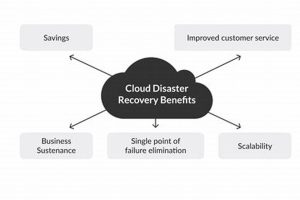
Minimizing service disruptions is a critical aspect of modern IT infrastructure. One approach focuses on eliminating single points of failure to ensure continuous operation, often through redundant systems and failover mechanisms. For... Read more »

The Community Development Block Grant (CDBG) program provides flexible funding to help communities address a wide range of development needs. A significant portion of CDBG funds can be allocated for disaster recovery,... Read more »
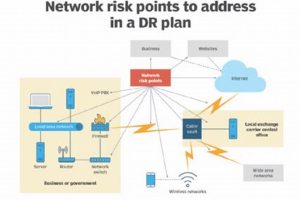
A documented process outlines procedures to restore network infrastructure and operations following an unforeseen disruptive event. For instance, after a cyberattack or natural disaster, this documentation guides organizations in recovering critical data,... Read more »
Protecting vital data and ensuring business continuity are paramount in today’s digital landscape. When critical IT infrastructure experiences unexpected disruptions, whether due to natural disasters, cyberattacks, or human error, organizations face potential... Read more »

A structured method for evaluating preparedness for operational disruptions involves systematically reviewing plans, procedures, and resources dedicated to restoring critical systems and data following significant unforeseen events. This method often utilizes a... Read more »