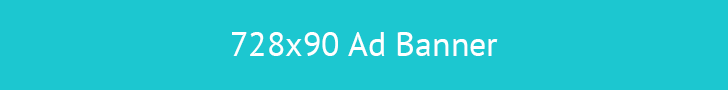
Protecting critical business operations relies on ensuring the continuous availability of essential platforms. For organizations that depend on ServiceNow for IT service management, HR, security, and other crucial functions, a robust plan... Read more »
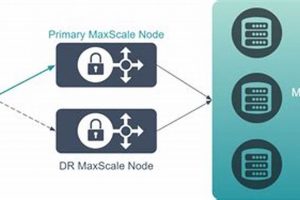
Data protection against catastrophic events is paramount for business continuity. A modern approach to this challenge utilizes a cloud data management platform that simplifies and automates the process of protecting, recovering, and... Read more »
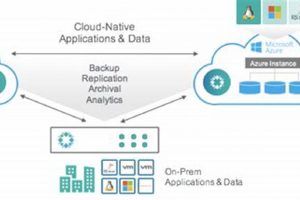
A documented, structured approach ensures business continuity in the face of disruptive events. This involves a pre-defined set of instructions and resources to restore critical IT systems, applications, and data. For example,... Read more »

The process of safeguarding an organization from the detrimental effects of significant disruptive events involves developing and implementing strategies to restore critical business functions and data. For example, a company might create... Read more »

Protecting digital assets involves two key processes: regularly copying information to a separate, secure location and having a comprehensive plan to restore functionality after unforeseen events. For example, a business might copy... Read more »

Protecting an organization’s digital assets and ensuring business continuity in the face of disruptive events, such as natural disasters, cyberattacks, or hardware failures, requires a robust plan. This involves implementing processes and... Read more »

Protecting organizational data and ensuring business continuity involves two key processes: restoring data and systems after a disruptive event, and routinely copying information to a separate location. For example, after a server... Read more »

Business continuity relies heavily on the ability to quickly restore data and applications following unforeseen events. A comprehensive solution combines robust backup capabilities with swift and reliable restoration procedures, enabling organizations to... Read more »

A documented process enabling an organization to resume mission-critical functions following a disruptive event, such as a natural disaster, cyberattack, or hardware failure, is crucial for business continuity. This process outlines procedures... Read more »
A robust strategy for restoring IT infrastructure and operations after a disruptive event typically involves several key elements. These elements include a comprehensive risk assessment to identify potential threats, a detailed recovery... Read more »