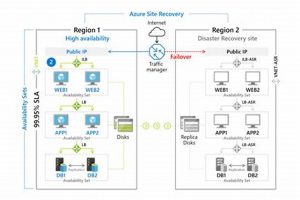
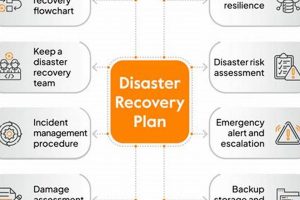
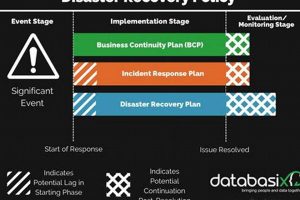
A pre-designed document providing a structured framework for restoring IT infrastructure and operations after an unforeseen disruptive event ensures business continuity by outlining procedures, responsibilities, and resources required for recovery. For example, a standardized document might detail system restoration steps, communication protocols, and data backup strategies for different disruption scenarios.
Maintaining operational resilience is paramount in today’s interconnected world. Such frameworks minimize downtime, data loss, and financial impact following disruptive incidents. A documented approach allows organizations to respond systematically, reducing confusion and accelerating the recovery process. The evolution of these frameworks reflects increasing reliance on technology and the growing complexity of IT systems. Preparedness facilitates a swift return to normal operations, safeguarding reputation and stakeholder trust.
The following sections will delve into the core components of a robust framework, best practices for development and implementation, and strategies for ongoing maintenance and testing.
Key Considerations for Disaster Recovery Planning
Developing an effective strategy for IT system restoration requires careful consideration of several crucial aspects. These tips offer guidance for establishing a robust framework.
Tip 1: Regular Risk Assessment: Conduct thorough and recurring evaluations of potential threats, vulnerabilities, and their potential impact. This informs prioritization and resource allocation.
Tip 2: Comprehensive Scope: Include all critical systems, applications, and data within the scope. Consider interdependencies and prioritize based on business impact.
Tip 3: Detailed Recovery Procedures: Document step-by-step instructions for system restoration, including specific technical configurations and dependencies.
Tip 4: Defined Roles and Responsibilities: Clearly outline individual responsibilities during a disaster scenario, ensuring accountability and efficient coordination.
Tip 5: Communication Plan: Establish communication protocols for internal teams, external stakeholders, and clients during a disruption, maintaining transparency and managing expectations.
Tip 6: Data Backup and Recovery: Implement robust backup and recovery mechanisms, ensuring data integrity and minimizing potential data loss.
Tip 7: Testing and Refinement: Regularly test and refine the documented procedures through simulations and drills to identify gaps and improve effectiveness.
Tip 8: Offsite Storage and Redundancy: Maintain offsite backups and redundant infrastructure to ensure accessibility and resilience in case of primary site failure.
Adopting these practices ensures a higher level of preparedness, enabling organizations to minimize downtime, protect critical data, and maintain business operations during unforeseen events.
By incorporating these key considerations, organizations can establish a robust framework that safeguards their IT infrastructure and ensures business continuity.
1. Predefined Structure
A predefined structure forms the backbone of an effective IT disaster recovery plan template. This structure provides a standardized framework, ensuring consistency and completeness in addressing all crucial aspects of recovery. Without a predefined structure, plans risk becoming disorganized, incomplete, and ultimately ineffective during a crisis. A structured template ensures all essential components, such as risk assessment, recovery procedures, communication protocols, and resource allocation, are systematically addressed. This organized approach facilitates efficient navigation and implementation during a high-pressure disaster scenario.
For example, a standardized template might categorize recovery procedures by system or application, allowing recovery teams to quickly locate relevant instructions. This structured approach minimizes confusion and accelerates restoration efforts. Furthermore, a predefined structure promotes consistency across different recovery plans within an organization, simplifying training and execution. Consider a multinational corporation with diverse IT infrastructure across various branches. A standardized template ensures consistent disaster recovery practices across all locations, streamlining responses and minimizing variability in recovery times.
Leveraging a predefined structure in IT disaster recovery planning translates to improved preparedness, reduced downtime, and minimized data loss during unforeseen events. This structured approach promotes efficient response and recovery, safeguarding business operations and minimizing financial impact. Challenges may include adapting standardized templates to unique organizational needs. However, the benefits of a structured approach significantly outweigh the challenges, making it a cornerstone of effective IT disaster recovery planning.
2. Documented Procedures
Documented procedures form a critical component of a robust IT disaster recovery plan template. A well-defined set of documented procedures provides clear, step-by-step instructions for responding to and recovering from IT disruptions. This clarity is essential for minimizing downtime and ensuring a consistent, predictable recovery process, regardless of personnel changes or the specific circumstances of the disruption. The absence of documented procedures can lead to confusion, delays, and inconsistent recovery efforts, potentially exacerbating the impact of the disaster. For example, imagine a scenario where a primary server fails. Without documented procedures, identifying the correct backup server, accessing necessary credentials, and initiating the restoration process can become significantly more complex and time-consuming.
A comprehensive IT disaster recovery plan template leverages documented procedures to address various aspects of recovery. These procedures may include instructions for data backup and restoration, system failover, communication protocols during an outage, and post-incident review processes. Specificity within these documented procedures is paramount. Consider a data restoration procedure. Instead of a general instruction to “restore data from backup,” a detailed procedure would specify the backup location, the restoration software to use, the required parameters, and the verification steps to confirm successful data restoration. This level of detail reduces ambiguity and ensures consistent execution, regardless of the individual performing the task. Another practical example involves communication protocols. Documented procedures might outline specific communication channels to use for internal teams, external stakeholders, and clients during a disruption. These procedures should include contact lists, escalation paths, and pre-approved messaging templates to ensure clear and consistent communication throughout the incident.
In conclusion, documented procedures are not merely a helpful addition to an IT disaster recovery plan template; they are an indispensable component. They ensure clarity, consistency, and efficiency in disaster response and recovery efforts. Challenges in maintaining up-to-date documentation can arise, particularly in dynamic IT environments. However, the benefits of clear, well-maintained documented procedures in minimizing downtime and ensuring business continuity far outweigh the challenges. This emphasis on documentation contributes significantly to the overall effectiveness of the disaster recovery plan, facilitating a swift and organized return to normal operations.
3. Resource Allocation
Effective disaster recovery hinges on appropriate resource allocation within the IT disaster recovery plan template. Pre-emptive allocation ensures the availability of essential resources during and after a disruptive event, minimizing downtime and facilitating efficient recovery. Without adequate resource allocation, recovery efforts can be severely hampered, leading to prolonged outages, data loss, and significant financial impact. This section explores key facets of resource allocation within disaster recovery planning.
- Hardware Resources
Recovery often requires access to backup servers, network devices, and storage systems. Pre-allocating or reserving these hardware resources ensures their availability when needed. For instance, an organization might maintain a dedicated set of standby servers in a geographically separate location, ready to take over operations in case of a primary data center outage. Failing to pre-allocate hardware can lead to delays in recovery while resources are procured or provisioned, potentially exacerbating the impact of the disruption.
- Software Resources
Recovery procedures rely on specific software tools for data backup, restoration, system replication, and communication. Ensuring access to licensed software, along with necessary configurations and documentation, is crucial. Consider a database server recovery scenario. The necessary database management software, backup and restoration tools, and any specialized scripting tools should be readily accessible to the recovery team. Overlooking software resource allocation can significantly impede recovery progress.
- Human Resources
Recovery requires skilled personnel to execute the plan, manage communications, and troubleshoot technical issues. Clearly defined roles and responsibilities, coupled with training and contact information, are essential. For instance, a designated team might be responsible for restoring database servers, while another team manages network connectivity. Clear roles and responsibilities ensure coordinated recovery efforts. Without assigned personnel, recovery tasks may lack clear ownership, leading to confusion and delays.
- Financial Resources
Disaster recovery incurs costs, including hardware and software procurement, personnel training, and ongoing maintenance. Allocating a budget specifically for disaster recovery ensures financial readiness when a disruption occurs. For example, an organization might allocate funds for maintaining offsite backup storage or subscribing to cloud-based disaster recovery services. Insufficient financial resources can restrict recovery options and prolong downtime.
Careful consideration of these facets of resource allocation within an IT disaster recovery plan template allows organizations to prepare effectively for unforeseen events. Adequate resource allocation streamlines recovery processes, minimizes downtime, and reduces the overall impact of IT disruptions. Proactive planning and resource allocation demonstrate a commitment to business continuity and minimize the potential financial and reputational damage associated with IT outages.
4. Responsibility Assignment
Clear responsibility assignment is a cornerstone of an effective IT disaster recovery plan template. Assigning specific roles and responsibilities ensures accountability and streamlines recovery efforts during a crisis. Without clearly defined ownership, tasks may be overlooked, leading to confusion, delays, and ultimately, a less effective recovery process. This section explores key facets of responsibility assignment within disaster recovery planning.
- Recovery Team Lead
The recovery team lead oversees all aspects of the disaster recovery process. This individual coordinates activities, makes critical decisions, and ensures communication flows effectively between teams and stakeholders. For example, during a server outage, the recovery team lead directs the restoration process, communicates updates to management, and coordinates with technical teams to resolve underlying issues. This centralized leadership ensures a coordinated and efficient response.
- Technical Specialists
Technical specialists possess the expertise to execute specific recovery tasks. These individuals might specialize in areas like database administration, network engineering, or system security. For instance, a database administrator would be responsible for restoring databases from backups, while a network engineer would focus on restoring network connectivity. Assigning responsibilities based on technical expertise ensures tasks are handled efficiently and effectively.
- Communication Lead
The communication lead manages all internal and external communications during a disaster. This individual keeps stakeholders informed of the situation, provides updates on recovery progress, and manages communication channels. For example, the communication lead might issue status reports to management, communicate with affected users, and coordinate with public relations teams. Centralized communication management prevents conflicting messages and ensures consistent information dissemination.
- Documentation and Reporting
Responsibility for documenting the disaster, recovery efforts, and lessons learned is crucial for future improvements. A designated individual or team meticulously records events, actions taken, and outcomes. This documentation informs post-incident reviews, identifies areas for improvement in the disaster recovery plan, and provides valuable insights for future planning. For example, documenting the timeline of a server outage, the steps taken to restore service, and the root cause of the outage helps refine recovery procedures and prevent future occurrences. This focus on documentation promotes continuous improvement and enhances the organization’s overall disaster recovery posture.
By clearly defining and assigning these responsibilities within the IT disaster recovery plan template, organizations establish a framework for efficient and effective responses to disruptive events. This structured approach ensures accountability, minimizes confusion during a crisis, and contributes significantly to a successful recovery process. Regularly reviewing and updating responsibility assignments, especially as technology and personnel change, maintains the plan’s effectiveness and ensures ongoing preparedness.
5. Communication Protocols
Effective communication is paramount during an IT disaster. A well-defined communication protocol within the IT disaster recovery plan template ensures timely and accurate information flow among stakeholders, minimizing confusion and facilitating coordinated recovery efforts. Without established communication protocols, misinformation can spread, hindering recovery and potentially exacerbating the impact of the disruption. This section explores key facets of communication protocols within disaster recovery planning.
- Target Audience Segmentation
Different stakeholders require different types of information. Communication protocols should segment target audiences, such as technical staff, management, clients, and the public, tailoring messages to their specific needs and informational requirements. For instance, technical teams need detailed updates on system status, while clients require assurances about service restoration timelines. Segmented communication prevents information overload and ensures each stakeholder group receives relevant updates.
- Communication Channels
Multiple communication channels should be established to ensure redundancy and reach diverse audiences. These channels might include email, SMS, dedicated communication platforms, conference calls, and social media updates. For example, during a network outage affecting email, SMS messages could provide critical updates to recovery teams. Diverse communication channels ensure message delivery even if some channels become unavailable during the disaster.
- Escalation Procedures
Clear escalation procedures ensure critical issues reach the appropriate personnel promptly. The plan should define reporting hierarchies and contact information for key decision-makers. For instance, if a critical system restoration fails, predefined escalation procedures ensure the issue is immediately escalated to senior technical staff and management for prompt resolution. Efficient escalation minimizes delays and facilitates timely decision-making.
- Frequency and Timing
Regular and timely communication updates build trust and manage expectations. The plan should specify communication frequency during various phases of recovery. For example, initial updates might be frequent to inform stakeholders of the situation and ongoing actions. As recovery progresses, updates might become less frequent but should remain consistent and informative. Regular communication maintains transparency and reassures stakeholders of ongoing efforts.
Integrating these communication protocols into the IT disaster recovery plan template establishes a framework for clear, consistent, and effective communication during a crisis. Well-defined communication protocols contribute significantly to a coordinated and efficient recovery process, minimizing disruption and maintaining stakeholder confidence. Regularly reviewing and updating communication protocols, incorporating feedback from stakeholders and incorporating lessons learned from past incidents, ensures the communication plan remains effective and aligned with evolving needs.
6. Testing and Refinement
A robust IT disaster recovery plan template requires rigorous testing and refinement to ensure its effectiveness in real-world scenarios. Testing validates the plan’s assumptions, identifies potential weaknesses, and provides opportunities for improvement. Without regular testing and subsequent refinement, a plan may prove inadequate during an actual disaster, potentially leading to prolonged downtime, data loss, and significant business disruption. This process is crucial for maintaining a current and effective disaster recovery posture.
- Simulated Disaster Scenarios
Simulated disaster scenarios, ranging from minor disruptions to full-scale outages, test the plan’s practicality and completeness. These simulations might involve a simulated server failure, network outage, or natural disaster. Running through these scenarios identifies potential gaps in procedures, resource allocation, or communication protocols. For example, a simulated server failure might reveal inadequate backup procedures or insufficient hardware resources at the recovery site. These simulations provide valuable insights for refining the plan.
- Regular Testing Cadence
Regular testing, conducted at predefined intervals, ensures the plan remains current and aligned with evolving IT infrastructure and business requirements. The frequency of testing depends on factors like the criticality of systems and the rate of change within the IT environment. More frequent testing is typically recommended for mission-critical systems. Regular testing, whether monthly, quarterly, or annually, ensures the plan remains a living document and adapts to changing needs.
- Post-Test Analysis and Refinement
Thorough post-test analysis identifies areas for improvement within the plan. This analysis reviews the effectiveness of procedures, communication protocols, resource allocation, and overall team performance. Identified weaknesses are then addressed through plan revisions, updated procedures, or additional training. For example, if communication breakdowns occurred during a test, the communication protocols within the plan might be revised to enhance clarity and efficiency. This iterative process of testing and refinement ensures continuous improvement.
- Documentation and Version Control
Maintaining comprehensive documentation of test results, identified weaknesses, and subsequent plan revisions is essential. Version control ensures clarity and traceability of changes made to the plan over time. This documentation provides valuable insights for future testing and refinement cycles. Clear documentation also ensures all stakeholders have access to the most current version of the plan, promoting consistency and preparedness. Version control facilitates tracking improvements and ensures all stakeholders are aware of the latest updates.
Regular testing and continuous refinement form a cyclical process crucial for maintaining a robust and effective IT disaster recovery plan. This ongoing process ensures the plan remains aligned with evolving IT infrastructure, business requirements, and potential threats. By incorporating these practices, organizations demonstrate a proactive approach to disaster recovery, minimizing potential downtime, data loss, and the associated financial and reputational risks. The commitment to testing and refinement underscores a dedication to business continuity and reinforces organizational resilience.
7. Regular Updates
Maintaining an effective IT disaster recovery plan template requires ongoing vigilance and adaptation. Regular updates ensure the plan remains aligned with the ever-evolving technological landscape and changing business requirements. A static, outdated plan offers limited protection against emerging threats and evolving system vulnerabilities. This section explores key facets of regular updates within disaster recovery planning.
- Hardware and Software Inventory
IT infrastructure undergoes constant change. Regular updates to the hardware and software inventory within the disaster recovery plan reflect these changes, ensuring accuracy and completeness. For example, new servers, software applications, and network devices should be documented, and decommissioned systems removed from the plan. Accurate inventory management ensures recovery procedures address the current state of the IT environment, preventing discrepancies during a disaster.
- Dependency Mapping
System interdependencies evolve as new technologies are integrated. Regularly updating dependency maps ensures the plan accurately reflects these relationships. Understanding these dependencies is crucial for prioritizing system restoration and minimizing cascading failures. For instance, if a database server relies on a specific authentication server, the plan should reflect this dependency, ensuring the authentication server is restored before the database server. Accurate dependency mapping streamlines recovery efforts and reduces the risk of unforeseen complications.
- Security Vulnerabilities and Patches
New security vulnerabilities emerge constantly. Regular updates incorporate the latest security patches and vulnerability mitigations into the disaster recovery plan. This ensures recovery procedures address current threats and minimize the risk of data breaches or system compromises during recovery. For example, if a critical vulnerability is discovered in a specific operating system, the plan should be updated to include patching procedures for affected systems during recovery. This proactive approach strengthens security posture during a vulnerable period.
- Contact Information and Personnel
Personnel changes and contact information updates require regular revisions within the plan. Ensuring contact lists, escalation paths, and responsibility assignments are current is essential for effective communication and coordination during a disaster. For example, if a key technical specialist leaves the organization, the plan should be updated to reflect the new contact person responsible for specific recovery tasks. Accurate contact information ensures timely communication and prevents delays during a crisis.
Regular updates transform the IT disaster recovery plan template from a static document into a dynamic tool aligned with current IT infrastructure, business needs, and emerging threats. This proactive approach to plan maintenance significantly enhances an organization’s ability to respond effectively to disruptions, minimize downtime, and protect critical data. Failing to maintain a current plan undermines its effectiveness, increasing the risk of prolonged outages and data loss. Regular updates demonstrate a commitment to business continuity and reinforce organizational resilience in the face of unforeseen events.
Frequently Asked Questions
This section addresses common inquiries regarding IT disaster recovery plan templates, providing clarity and guidance for organizations seeking to enhance their preparedness for unforeseen events.
Question 1: How often should an IT disaster recovery plan template be reviewed and updated?
Review and update frequency depends on the rate of change within the IT environment and the organization’s risk tolerance. A minimum annual review is recommended, with more frequent updatesquarterly or even monthlyfor organizations with rapidly evolving infrastructure or higher risk profiles. Significant changes in infrastructure, applications, or business processes necessitate immediate plan revisions.
Question 2: What are the key components of an effective IT disaster recovery plan template?
Essential components include a documented risk assessment, detailed recovery procedures, clearly defined roles and responsibilities, communication protocols, data backup and restoration strategies, testing and refinement procedures, and a plan for regular updates.
Question 3: What are the common pitfalls to avoid when developing an IT disaster recovery plan template?
Common pitfalls include failing to adequately assess risks, overlooking system interdependencies, neglecting to test the plan regularly, not assigning clear responsibilities, and failing to keep the plan updated with evolving infrastructure and business needs.
Question 4: What is the difference between a disaster recovery plan and a business continuity plan?
A disaster recovery plan focuses specifically on restoring IT infrastructure and operations after a disruption. A business continuity plan encompasses a broader scope, addressing overall business operations and ensuring continuity of essential functions during and after a disruption, including non-IT related processes.
Question 5: How can organizations ensure their IT disaster recovery plan remains effective over time?
Regular testing, continuous refinement based on lessons learned, and ongoing updates to reflect changes in IT infrastructure, applications, and business processes are crucial for maintaining an effective IT disaster recovery plan.
Question 6: What are the potential consequences of not having an IT disaster recovery plan?
Lack of a plan can lead to extended downtime, significant data loss, financial losses due to business interruption, reputational damage, and potential legal liabilities. Preparedness minimizes these risks and facilitates a swift return to normal operations.
Proactive planning and a commitment to regular review and updates are essential for ensuring the effectiveness of an IT disaster recovery plan. Preparedness minimizes the impact of unforeseen events and safeguards business operations.
For further guidance on developing and implementing a comprehensive IT disaster recovery plan, consult industry best practices and seek expert advice if needed.
Conclusion
Exploration of IT disaster recovery plan templates reveals their crucial role in maintaining business continuity. Key elements include a structured framework, documented procedures, resource allocation, defined responsibilities, and established communication protocols. Regular testing and refinement, coupled with ongoing updates reflecting evolving IT infrastructure and potential threats, ensure effectiveness. These frameworks enable organizations to respond systematically to disruptions, minimizing downtime, data loss, and financial repercussions.
Effective disaster recovery planning requires a proactive and adaptable approach. Organizations must recognize the dynamic nature of IT environments and commit to ongoing maintenance and refinement of their disaster recovery strategies. A robust IT disaster recovery plan template, diligently maintained and tested, forms the bedrock of organizational resilience, safeguarding critical data, operations, and long-term stability in an increasingly interconnected and unpredictable world.