Data protection involves two distinct but related concepts: creating copies of data and restoring access to IT infrastructure after an outage. The former focuses on preserving information by regularly copying files and... Read more »
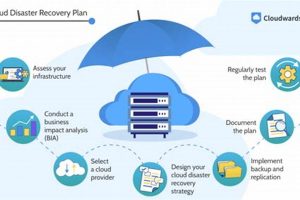
Protecting organizational data and ensuring business continuity are paramount in today’s digital landscape. A strategy involving offsite data replication to a secure, remote server infrastructure, commonly referred to as “the cloud,” allows... Read more »
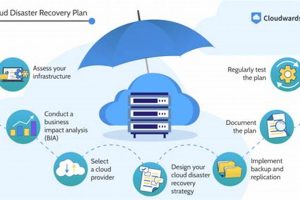
Protecting organizational data and ensuring business continuity are paramount in today’s digital landscape. This involves replicating and storing information on remote servers accessed via the internet. For example, a company might store... Read more »

Protecting an organization’s data and ensuring its operational continuity are paramount in today’s business landscape. Strategies and technologies that enable the restoration of IT infrastructure and data after disruptive events, such as... Read more »
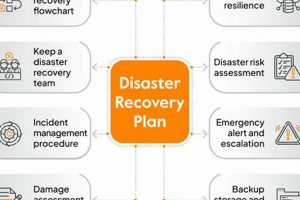
A comprehensive strategy for ensuring business continuity involves preparing for and recovering from significant disruptions. This involves regularly copying critical data and systems, establishing a documented procedure for restoring functionality in a... Read more »

Protecting organizational data and ensuring business continuity involves implementing strategies that address potential disruptions. These strategies encompass creating redundant copies of data and establishing procedures to restore systems and operations following unforeseen... Read more »
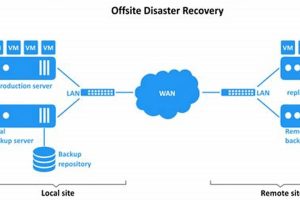
Protecting vital information assets requires a comprehensive strategy involving the duplication and relocation of data to a separate physical location. This process ensures business continuity by safeguarding against data loss from various... Read more »

Protecting vital data and ensuring business continuity are paramount in today’s digital landscape. A strategy utilizing offsite servers to store copies of critical data and applications enables restoration of systems and operations... Read more »

Protecting vital data and ensuring business continuity involves systematic data copying and reliable restoration procedures. This typically includes a third-party service provider assuming responsibility for implementing, administering, and supporting the entire process.... Read more »

Protecting organizational data and ensuring business continuity involves implementing a robust system for replicating and storing information in a secure, offsite location. This process allows for the restoration of critical systems and... Read more »