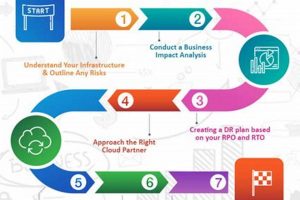
A documented process enabling the restoration of IT infrastructure and operations following a disruptive event impacting cloud-based systems ensures business continuity by outlining procedures for data backup, recovery, and failover to alternate... Read more »
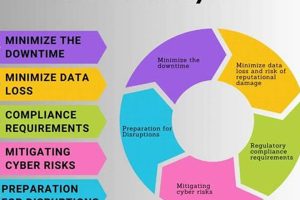
A structured approach that ensures an organization’s ability to resume operations quickly following disruptive events, such as natural disasters, cyberattacks, or equipment failures, is critical. This involves defining processes, procedures, and resources... Read more »
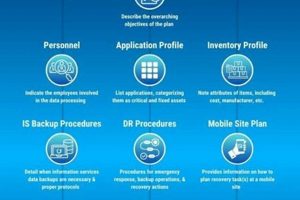
The primary aims of such a plan are to minimize disruptions to business operations in the event of unforeseen circumstances, such as natural disasters, cyberattacks, or hardware failures. A well-constructed plan enables... Read more »
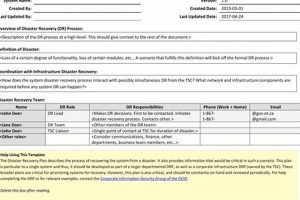
A template for restoring data and IT infrastructure after an unforeseen disruption, often offered in a portable document format, provides a concrete starting point for organizations to customize their approach to business... Read more »
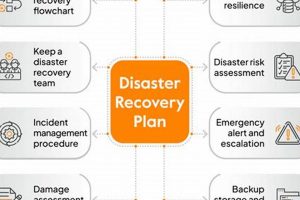
A strategy for restoring IT infrastructure and operations after an unforeseen disruptive event is essential for any organization. This involves documented procedures and resources allocated to minimize downtime and data loss in... Read more »

A pre-designed framework for creating a documented strategy to restore IT infrastructure and operations after an unforeseen disruptive event provides a structured approach to minimizing downtime and data loss. This framework often... Read more »

One approach addresses specific disruptions to normal operations, such as security breaches, system failures, or denial-of-service attacks. It focuses on containing the damage, restoring functionality quickly, and investigating the root cause to... Read more »

A structured strategy addressing potential emergencies, whether natural or human-made, outlines preemptive measures, immediate actions, and long-term recovery efforts. A municipality’s strategy for a major earthquake could include evacuation routes, designated shelters,... Read more »

Pre-designed documents providing a framework for restoring IT infrastructure and operations after disruptive events offer organizations a structured approach to business continuity. These frameworks typically include sections for risk assessment, recovery procedures,... Read more »

A pre-formatted document designed to guide households in preparing for and responding to emergencies provides a structured approach to enhancing safety and resilience. This typically includes sections for contact information, evacuation routes,... Read more »