A documented process outlines how to restore critical business software functionality following an unplanned outage. This process typically involves establishing redundant systems and data backups, defining recovery time objectives (RTOs) and recovery... Read more »

A robust strategy for restoring IT infrastructure and operations after an unforeseen disruption, such as a natural disaster, cyberattack, or equipment failure, is essential for any organization. This strategy typically involves a... Read more »
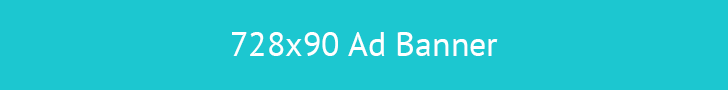
A robust strategy for business continuity and data protection in the Microsoft cloud environment involves establishing procedures and infrastructure to restore services following unexpected outages. This typically includes replicating crucial virtual machines,... Read more »
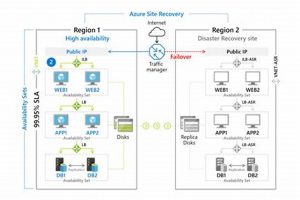
A structured approach that addresses the restoration of data, applications, and infrastructure following a security incident, such as a ransomware attack or data breach, is critical for organizational continuity. This approach typically... Read more »
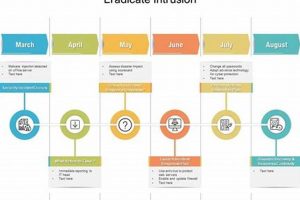
A sample blueprint for restoring network infrastructure and operations following an unforeseen disruption, such as a natural disaster or cyberattack, provides a concrete illustration of how an organization can prepare for and... Read more »
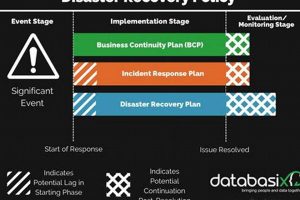
A documented set of procedures designed to restore an organization’s IT infrastructure and operations after an unforeseen disruptive event typically outlines recovery time objectives (RTOs) and recovery point objectives (RPOs), specifying the... Read more »

A comprehensive document outlining steps to restore IT infrastructure and operations following a disruptive event, such as a natural disaster, cyberattack, or hardware failure, is essential for business continuity. This document typically... Read more »

A well-structured strategy for restoring business operations after unforeseen disruptive events, such as natural disasters or cyberattacks, is paramount. This strategy typically outlines procedures for data backup and restoration, alternative work arrangements,... Read more »

A formalized strategy encompassing procedures and guidelines designed to mitigate the negative impacts of unforeseen disruptive events is essential for any organization or community. Such a strategy typically outlines specific actions to... Read more »
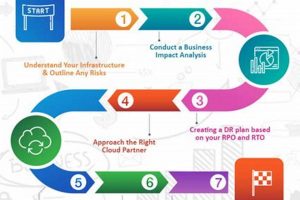
A documented process enabling the restoration of IT infrastructure and operations following a disruptive event impacting cloud-based systems ensures business continuity by outlining procedures for data backup, recovery, and failover to alternate... Read more »