A documented strategy designed to restore data and systems after a cyberattack involving malicious software that encrypts files and demands payment for their release involves several key components. These components typically include... Read more »
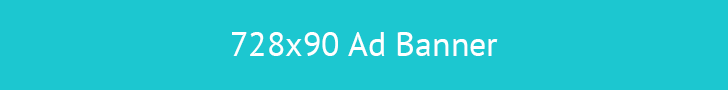
A comprehensive strategy for ensuring organizational resilience involves two key components: restoring IT infrastructure and operations after a disruptive event, and maintaining essential business functions during and after such an incident. A... Read more »
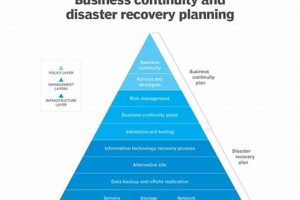
A documented process enabling the restoration of critical IT infrastructure and systems following a disruptive event, such as a natural disaster, cyberattack, or equipment failure, is essential for business continuity. This process... Read more »

A formalized strategy encompassing preparedness, response, and recovery measures designed to mitigate the impact of unforeseen adverse events, ranging from localized incidents to large-scale catastrophes, forms the bedrock of organizational and community... Read more »
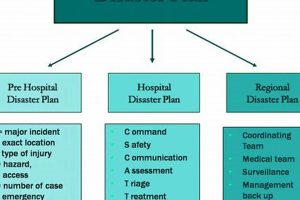
A predefined strategy encompassing procedures and protocols designed to safeguard staff, patients, and infrastructure during unforeseen critical incidents. For instance, such a strategy would detail how a facility manages patient surges during... Read more »

A sample strategy for restoring IT infrastructure and operations after a disruptive event typically includes elements such as identifying critical systems, establishing recovery time objectives, outlining backup procedures, and defining communication protocols.... Read more »

A pre-designed blueprint for restoring IT infrastructure and operations after an unforeseen disruptive event, such as a natural disaster or cyberattack, demonstrates how an organization can systematically resume critical functions. A sample... Read more »
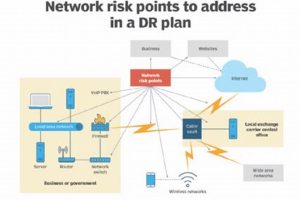
A documented process outlines procedures to restore network infrastructure and operations following an unforeseen disruptive event. For instance, after a cyberattack or natural disaster, this documentation guides organizations in recovering critical data,... Read more »
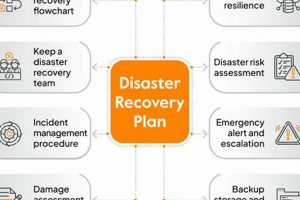
A comprehensive strategy for ensuring business continuity involves preparing for and recovering from significant disruptions. This involves regularly copying critical data and systems, establishing a documented procedure for restoring functionality in a... Read more »
![Best Disaster Plan Examples & Templates [Free Download] Disaster Information Hub – Latest Natural Disaster News & Emergency Resources Best Disaster Plan Examples & Templates [Free Download] | Disaster Information Hub – Latest Natural Disaster News & Emergency Resources](https://disastertw.com/wp-content/uploads/2025/09/th-87-300x200.jpg)
Disaster Plan Examples & Templates [Free Download]" width="100%" style="margin-right: 8px;margin-bottom: 8px;" /> A pre-designed template for addressing emergencies, typically including steps for preparedness, response, recovery, and mitigation, serves as a model for... Read more »