A strategy designed to restore data and systems following a ransomware attack is critical for business continuity. This involves a structured approach that outlines procedures for identifying the attack, isolating affected systems,... Read more »

A documented strategy designed to restore data and systems after a cyberattack involving malicious software that encrypts files and demands payment for their release involves several key components. These components typically include... Read more »
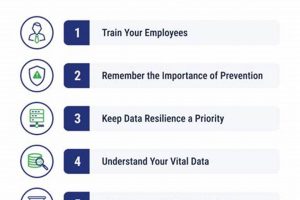
Protecting an organization’s data and operations from malicious software that encrypts files and demands payment for their release requires a specific, proactive strategy. This strategy involves documented procedures and resources that enable... Read more »

Protecting an organization’s data and systems against malicious encryption attacks that disrupt operations and demand payment for restoration is a critical aspect of business continuity. Imagine a scenario where crucial files are... Read more »

The process of restoring data and systems following a ransomware attack involves a multifaceted approach. This typically includes restoring from backups, eradicating the malicious software, and implementing security enhancements to prevent future... Read more »