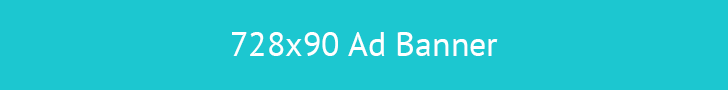
A specialized group responsible for planning, implementing, and managing restorative processes following disruptive events within Kruger National Park could encompass various skill sets, from wildlife management and infrastructure repair to communication and... Read more »
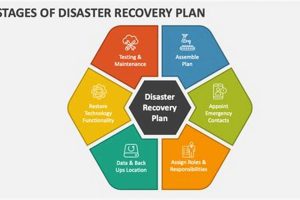
A structured approach to restoring IT infrastructure and operations following a disruptive event involves a sequence of carefully planned actions. For instance, a company might establish a procedure that begins with assessing... Read more »

A pre-designed framework for restoring essential operations after unforeseen events provides a structured approach for companies with limited resources to resume functionality quickly and efficiently. This framework typically includes pre-populated sections for... Read more »

Decoupling physical hardware from operating systems and applications allows for rapid recovery of IT infrastructure after unforeseen events. For example, virtual machines (VMs) representing servers, desktops, or even entire networks can be... Read more »
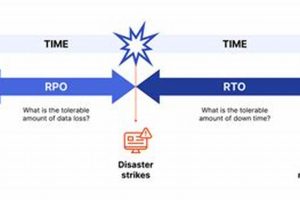
Recovery Time Objective (RTO) and Recovery Point Objective (RPO) are two crucial metrics used in disaster recovery planning. RTO signifies the maximum acceptable duration for restoring IT systems after a disruption. For... Read more »
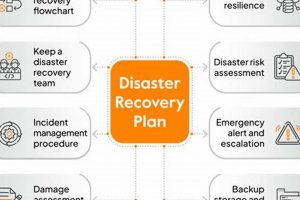
Protection for business continuity expenses incurred when activating a documented strategy to restore operations after unforeseen events, like natural disasters or cyberattacks, is a critical aspect of risk management. For instance, this... Read more »
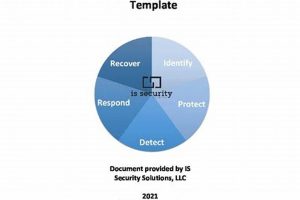
A framework provided by the National Institute of Standards and Technology (NIST) assists organizations in developing documented strategies for resuming operations after disruptive events. This framework offers guidance and a structured approach... Read more »

The restoration of data centers and IT infrastructure after disruptive events, encompassing hardware repair, data retrieval, and environmental remediation, forms the core of business continuity and resilience. For example, a specialized firm... Read more »
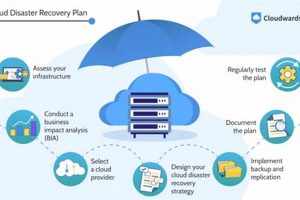
Protecting vital data and ensuring business continuity in the face of unforeseen events is paramount in today’s digital landscape. A robust strategy involving replicating and restoring data and applications hosted in a... Read more »

A planned simulation of emergency procedures assesses an organization’s ability to respond to significant disruptions. For example, such a simulation might involve restoring data from backups, activating alternate work locations, or testing... Read more »